TryHackMe - REloaded (Writeup by Isira Adithya)
So, I am Isira Adithya. I am a 16 years old student from Sri Lanka and I do not know lot about Ethical Hacking Stuff. Currently, I still learning about hacking and using Tryhackme to learn more.
This is the link of the room -> REloaded
So, Let's Start. I used below tools and softwares to solve this.
- Windows 10 (Operating System)
- Ghidra (Reverse Engineering Tool From NSA) (Download)
- Immunity Debugger v1.85 (Debugger) (Official Page - Download)
- WSL (Windows Subsystem For Linux) (How to install WSL on Windows 10) *Not Important
Task #1 (Level-0.exe)
This is very easy. Just run strings command against the binary. Use grep to filter the output. Flag is longer than 10 characters (look at the try hackme page), so I am going use below command.
strings Level-0.exe | grep -E '.{10,100}'
I am using a Regular Expression to filter strings between 10 to 100 characters.
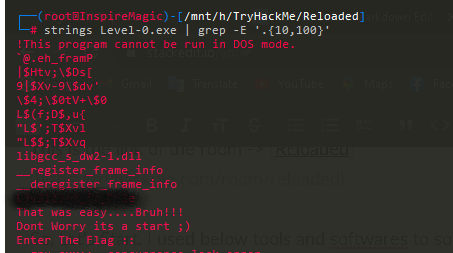
Just like that we can find the flag.
Task #2 (Level-1.exe)
Same as before. Just run strings command against the binary. But this time we cannot find any flags there.
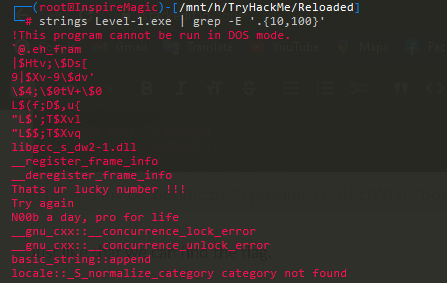
Note that there is a String, "Thats ur lucky number !!!". Now we can find this string in the memory and trace it back to find out how it works.
- Now load the binary into Ghidra. (It will take some time to analyze the binary.)
- Search for "Thats ur lucky number !!!" (Press S)
- Then find references to that address. (RClick -> References -> Show References To That ...)
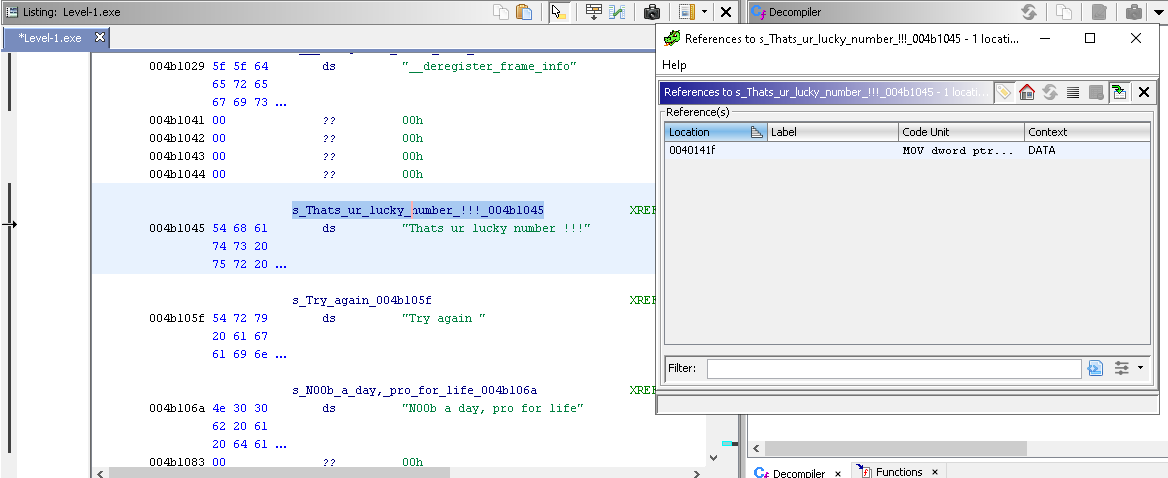
- Once you find that function. Ghidra will decompile that function to a C code. In that C code You will see that the program is comparing our input to a Number(HEX). Copy that hex number and convert it to decimal using Python or Cyberchef or any other method.
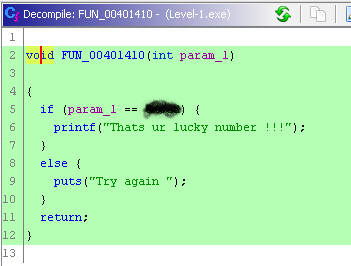
- That is the flag 👍.
Task #3 (Level-2.exe)
Same as before Run Strings command against the binary and you will find that once the program is patched it will output Get Ready For L4 ;) Load the binary into Ghidra and find the function using that string.
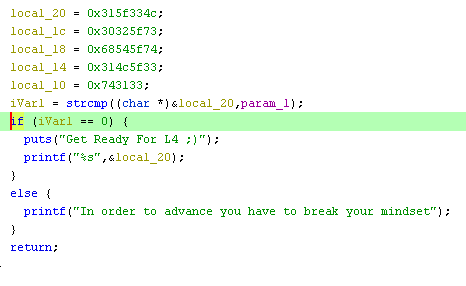
As you can see it compares the input with local_20 variable.
BTW, we have to patch this binary. So let's move on. Find the Assembly part of the code.
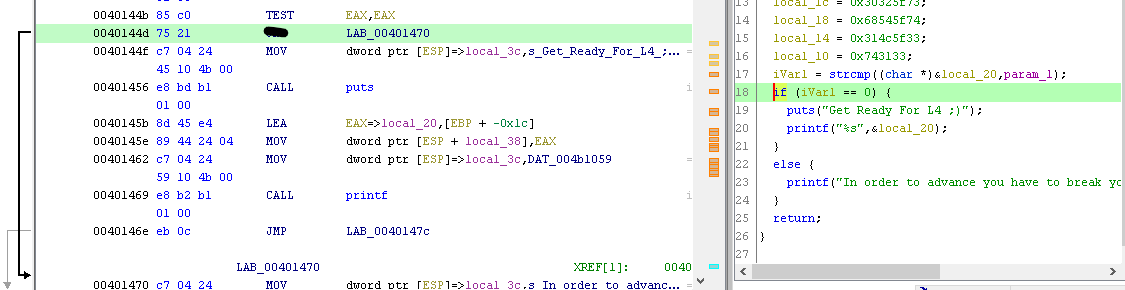
You can see that Instruction is redirecting us to failure message. If we modify that Instruction to something different (You can find it with little bit of googling) and then when we input a wrong argument it will display the flag.
Use Rclick -> Patch Instruction to change it.
Now use ghidra_SavePatch to save the patched file. Do not use Ghidra's export function (It is not working). Now try running it with a wrong argument.
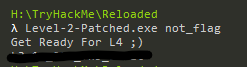
👍
Task #4 (Level-3.exe)
Same as before, Run strings command against the binary and you will find Rooted !!! string there. So, That means if we entered the correct flag it will output Rooted !!!.
Now Find Rooted !!! in the memory in Ghidra. Now you can see the function as C code in Ghidra.
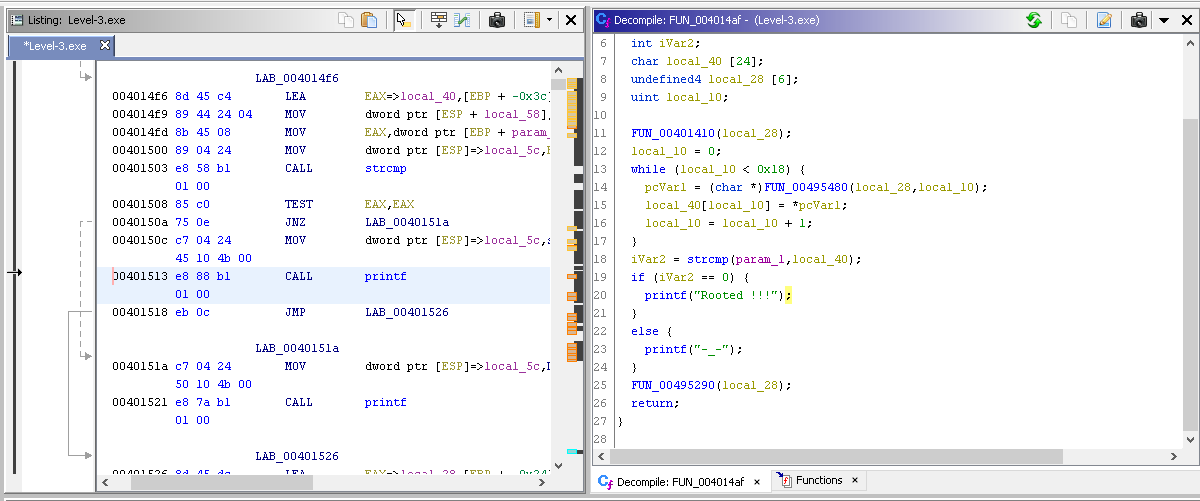
Remember that in this task we have to find Master Password. Looking at the C code tells that the Master Password is located at local_40 variable. We can either patch this program to output the master password or We can use Immunity Debugger to reveal the real password when it is executing via memory. Also, That while loop is changing the variable (XOR). So we have to look into memory before the loop begins.
Now, select any line above while loop and remember it's memory address.
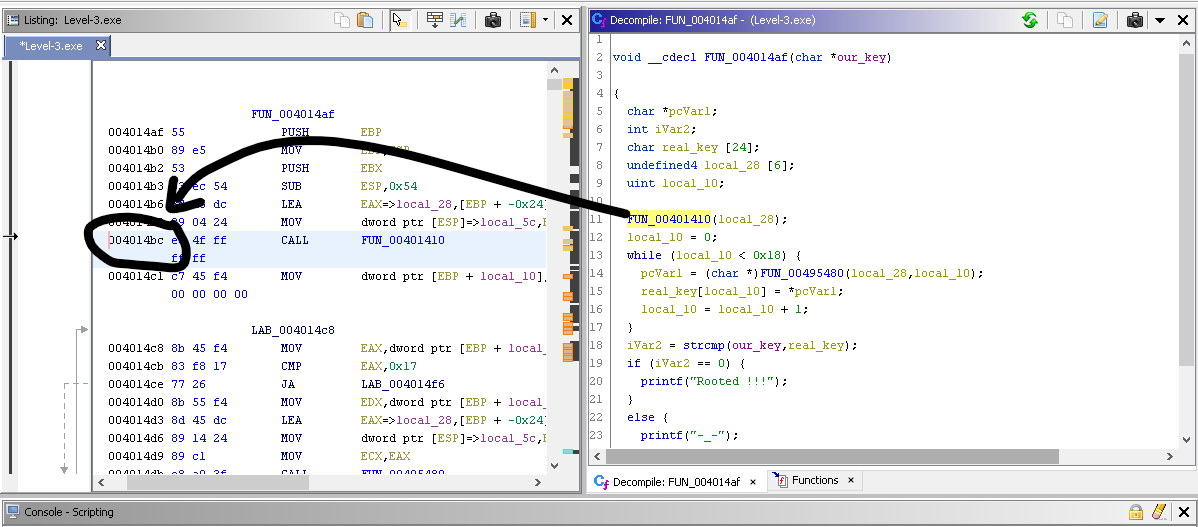
Load the binary into the Immunity Debugger and Make a breakpoint (Press F2) at that memory address.
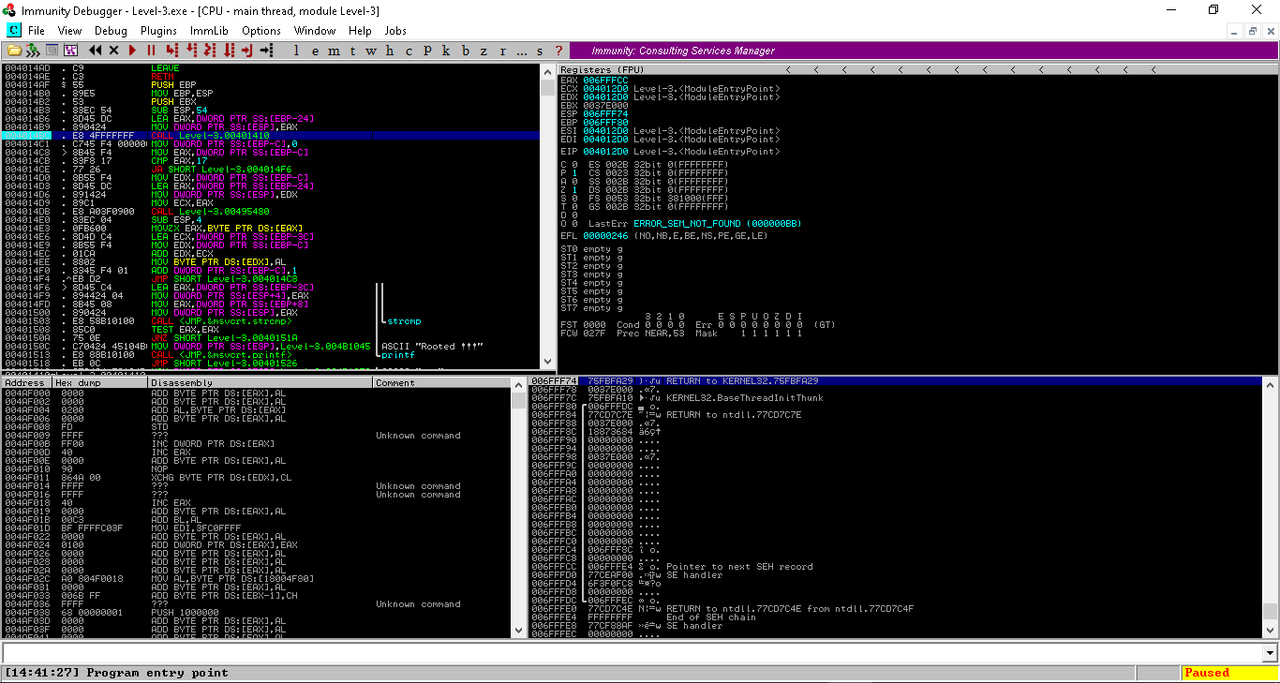
After that Press F9 to Run. Then enter something (a Wrong Password) in the program and hit enter. Immunity Debugger will pause the execution at the breakpoint. Now Check the Registers and the Stack. If you cannot find the flag there try Pressing F7 it will step into the next memory address. Repeat this until you see the Flag. Now submit the flag to TryHackMe and Press F7 Until you see the Master Password.
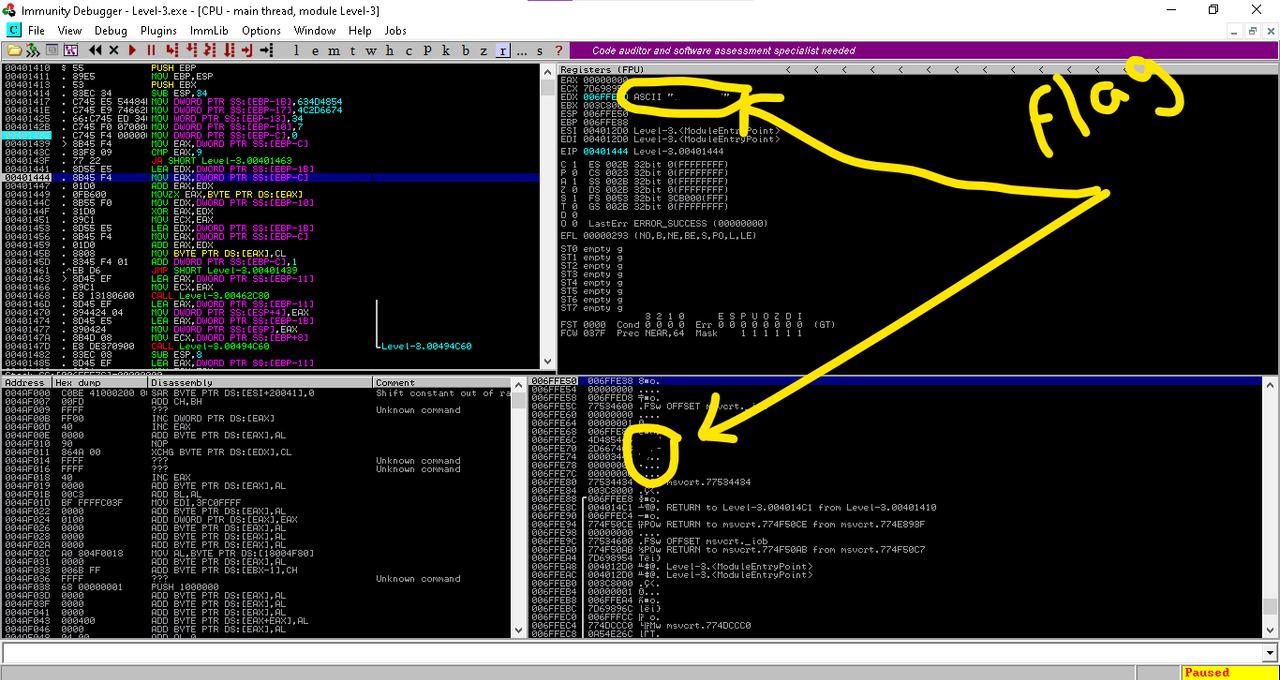
That's it! 👍
Task #5 (Level-4.exe)
This is a difficult one. There are nothing valuable strings inside the binary file. Also when we run the program it outputs Amcm↨QBu^YP+`lD↨V1pvY^BdR which is weird. This is encrypted with some sort of algorithm. So let's find out what that is.
Load the binary into the Ghidra. And find when we are using the printf function.
Symbol Tree -> Functions -> printf
Now Find where printf is used. (Find References) You will find a function similar to this.

Now you can see that it is printing param_1 variable which is passed when the function is called. Now find references of that FUN_00401453 function.
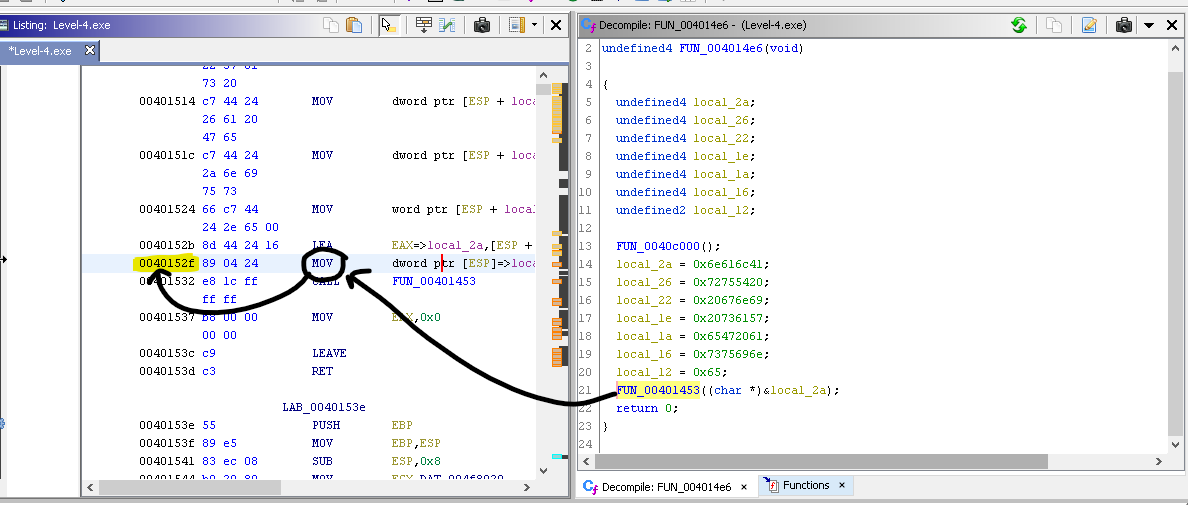
Now, Remember the memory address of that function call. (MOV) Above picture will explain it better than typing.
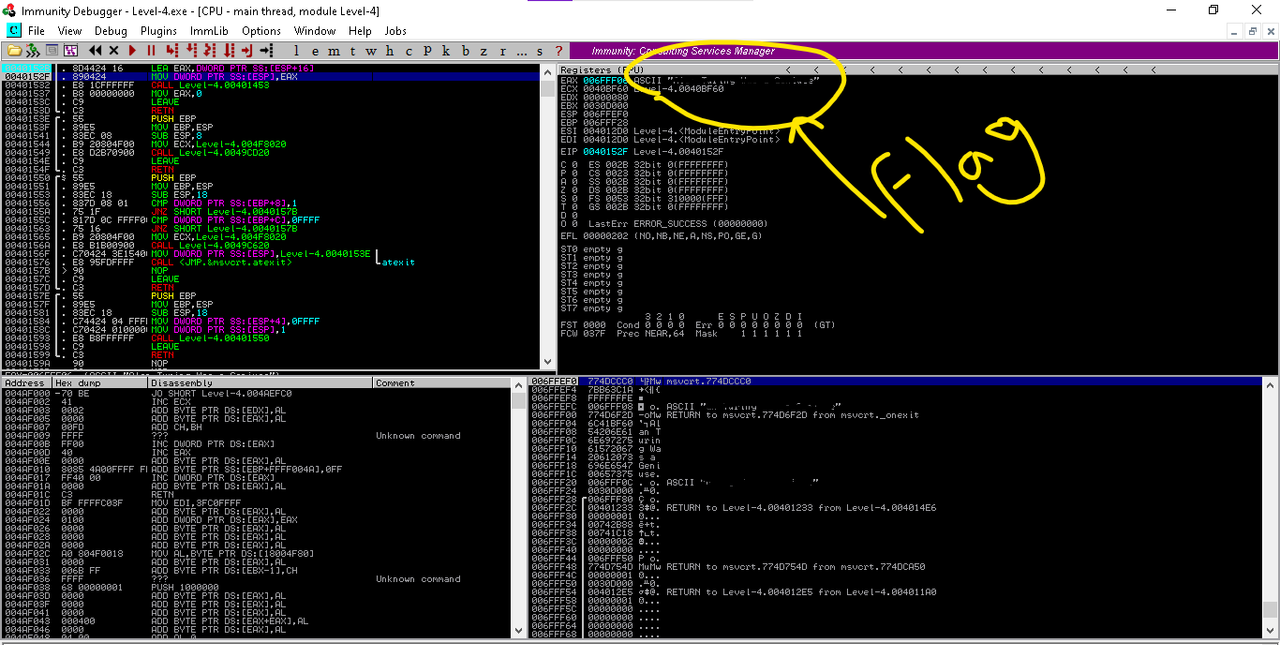
Now same as before load the binary into the Immunity Debugger and try to detect the flag. Submit it to the Tryhackme and now let's find out the algorithm.
I will reverse engineer the algorithm later. I have a exam to face next week.
Thanks for reading.
Bye. 👋🏽