My first bug - Reflected XSS
I think every hacker gets super excited when he/she found his/her first bug in the wild.
Whoami
Hey 👋🏽, I am Isira Adithya Ruwanpathirana and I am a 16 years old ethical hacker from Sri-Lanka.
My ethical hacking background
I don't have CEH / OSCP or any other thing to prove me as an hacker. I am a CTF Player and I love to play TryHackMe, Hackthebox and other CTFs. Recently, I came to know about the Intigriti XSS Challenge. I saw a couple of videos on the youtube and they were super hard. I was excited to try. Recently (03/2021), I saw the 0321 XSS Challenge by Intigriti and I started to compete. But, I tried about 5 days to get an XSS alert popup in the page 😅. But, It was a great challenge and I won some swag too. 🥳 So, Thanks 🙏🏽 Intigriti for motivating me.
How I found the bug
I got some private invitations as soon as I completed the XSS challenge by the Intigriti. It was a web hosting company but I cannot disclose any details futher than that. They also gave me a 300 euro voucher to buy a web hosting package on their web site.
When I started to explore the platform, It looked like almost perfect. About 2 days no luck, But, there was a feature to search mail accounts in the web hosting package.
I tried searching test123<>""''. That's my test to detect XSS.
I saw the word was injected in several places inside the page and <, >, ", '. It was almost impossible to inject any HTML tags and " character. They were encoded properly.
The bug
I realized that there was a AJAX function designed to the page or searching/filtering mail boxes and I saw that the URL is reflecting there.
But, the case was bug was that the URL relected inside a string declared using ' character. That was 👌🏽.
The Javascript Function
$(this).ajaxPost('/product/email/mailboxes/testdomain-intigriti-isira_com/?login=test123', {
data: {action: 'deletemailbox', recordid: elm.attr('title')},
success: function(response){
$(elm).parent().parent().slideUp('pbtn1', function(){ $(elm).parent().parent().remove(); });
}
});
So, I was super excited about this and I tried to exploit it. In about 30 minutes I realized a way to exploit the bug. I still don't know why '-alert(1)-' didn't work 🤔. If you guys know please help me via the comment section. Then, I sent my payload as a parameter to the ajaxPost function. The payload was ',alert(1),'.
When Injected the payload ( ',alert(1),' )
$(this).ajaxPost('/product/email/mailboxes/testdomain-intigriti-isira_com/?login=test',alert(1),'', {
data: {action: 'deletemailbox', recordid: elm.attr('title')},
success: function(response){
$(elm).parent().parent().slideUp('pbtn1', function(){ $(elm).parent().parent().remove(); });
}
});
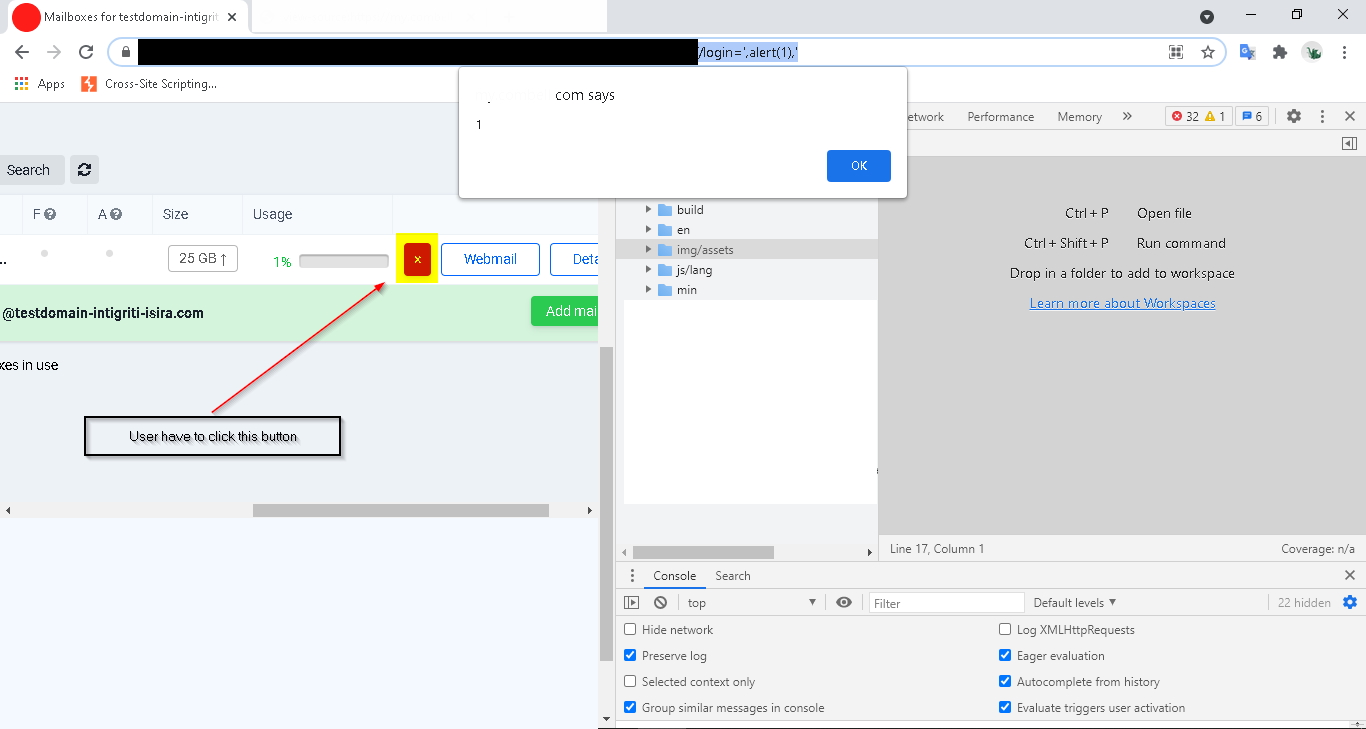
A screenshot (Intense Editing to hide the identity 😅)
The Report
I quickly went to the Intigriti to report this. This was my first report and I was quiet nervious about it. I did my best to write the report. The Program was offering 150EURO for reflected XSS (Medium Severity). But, to exploit the user correctly, We need the user interaction. By the way, that javascript code was inside a onclick listener. User had to click on the delete mailbox button to fire the XSS. So, Intigriti measured the impact and it was 4.2 MEDIUM. I was very happy to see that. Next day, The company reached to me and rewarded the bounty, that was my first bounty.
Notes
This was a private program at the time I tested this. I am not disclosing any details about the company and the Javascript code I showed is a fake one but it is good to demonstrate the bug. I came across 2 more bugs from this private program too.
Thanks
Thanks for reading this! 🙏🏽